Six of my top networking tools
Six tools that I use incredibly regularly when administering networks.
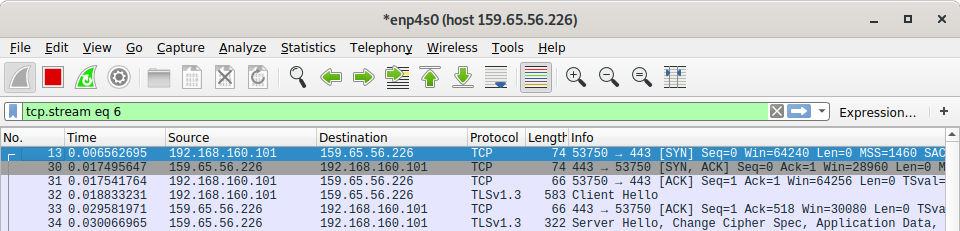
I find it interesting to see what tools others in the industry use, and have discovered many useful tools by watching others on YouTube or reading their blogs. Here I'm going to look at six of the tools I use regularly, and I recommend them to you if you work in networking or cyber security.
I'm going to start with some less technical tools that are, nonetheless, indispensable for my day job.
Nslookup
nslookup is used to translate a Domain Name System (DNS) name into an Internet Protocol (IP) address that's actually used by computers to route traffic. If you cannot resolve (translate) a DNS name then you won't be able to access the resource - simple.
By using nslookup it's possible to check the DNS name is actually valid based on your current network configuration. Most often I'm using this to check an address I've just created on my DNS server, or I'm checking an address I've been passed is correct before proceeding with a support ticket.
> nslookup blog.jonsdocs.org.uk
Server: 100.115.92.193
Address: 100.115.92.193#53
Non-authoritative answer:
Name: blog.jonsdocs.org.uk
Address: 104.31.86.17
Name: blog.jonsdocs.org.uk
Address: 104.31.87.17There's a new tool, dig, that replaces nslookup and can give more detail, however, nslookup is still more widely available (it's built in to a lot of Operating Systems (OS) by default).
Ping
Ping, the "Packet INternet Groper", is a basic utility used to check communication between two networked devices. Issuing a simple ping command will immediately tell you if the remote host is alive, well, almost.
> ping 8.8.8.8
PING 8.8.8.8 (8.8.8.8) 56(84) bytes of data.
64 bytes from 8.8.8.8: icmp_seq=1 ttl=53 time=14.4 ms
64 bytes from 8.8.8.8: icmp_seq=2 ttl=53 time=14.7 ms
--- 8.8.8.8 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1001ms
rtt min/avg/max/mdev = 14.402/14.598/14.794/0.196 msTo be accurate, ping will tell you if the remote device responds to ping - that's not the same thing as whether or not the remote device is alive. The additional information provided in the ping response can also tell us something about the remote device - more on that another time.
Usefully, ping will look at the system's hosts file before it performs a DNS lookup. To give a bit of history, before DNS existed services were located by looking up addresses in a list, the hosts file. As you can imagine, this soon became unmanageable but the file still exists ( /etc/hosts on Linux and C:\windows\system32\drivers\etc\hosts on Windows). Because ping looks in the hosts file we can easily check for a difference between DNS and our local system (our system's DNS lookup for a service may have been overridden by a hosts file entry).
Tracert / traceroute
These are the same tool, but on different OSes. Windows calls the tool tracert whereas Linux uses traceroute but in each case the purpose is to show how traffic gets from the device you run the command on to a remote device.
> traceroute -n 8.8.8.8
traceroute to 8.8.8.8 (8.8.8.8), 30 hops max, 60 byte packets
1 192.168.1.1 0.422 ms 0.573 ms 0.742 ms
2 84.93.253.64 9.392 ms 9.439 ms 10.242 ms
3 84.93.253.67 11.383 ms 11.419 ms 12.329 ms
4 195.99.125.132 12.575 ms 195.99.125.140 12.448 ms 195.99.125.132 12.422 ms
5 62.172.103.202 13.966 ms 109.159.252.80 14.011 ms 62.172.103.252 14.067 ms
6 109.159.253.185 14.406 ms 109.159.253.187 14.018 ms 195.99.126.77 13.802 ms
7 * * *
8 8.8.8.8 10.215 ms 10.287 ms 10.288 ms
traceroute on my Linux machine showing the path to Google's DNS server.By using traceroute I can check to see if traffic is flowing as designed (or as expected) on my network. Sometimes when a link goes down we'll lose access to a particular destination and traceroute can be really handy for showing that, especially if the traffic is sent back and forth between the same two points.
Wireshark
Wireshark is a network traffic protocol analyser and is available free from their website plus in numerous Linux distribution repositories. If you remember Ethereal from days gone by, this is the same tool following a rename.
During investigation of problems I find Wireshark is my go-to tool. If I'm receiving reports that a firewall rule I've created doesn't work I'll temporarily install Wireshark on the destination server to prove if the traffic is, or isn't, getting there. It's also possible to filter the view to show a specific conversation, so I can focus on a particular exchange.
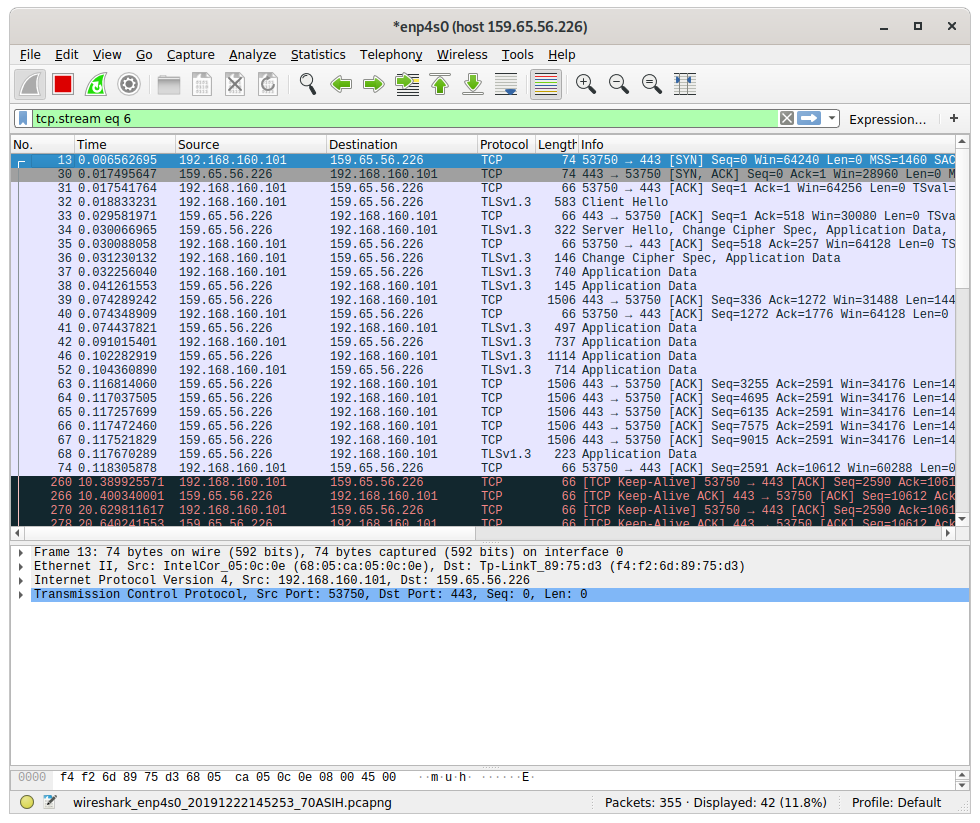
I've blogged about using Wireshark for troubleshooting before.
Nmap
Nmap is a fantastic tool for port scanning an IP range, but its uses don't just stop there. By extending functionality with the Nmap Scripting Engine (based on Lua) it's possible to make Nmap do much more, and there's plenty of scripts included in the base distribution. Want to enumerate shares on a Windows file server? No problem, there's a script for that.
Before I issue an IP to a device I use Nmap to scan for that IP first, to check it really is free. Ping isn't going to cut it here, as the device might simply not respond to ping, so I use a TCP SYN scan to attempt a connection to a number of ports known to be in use in our environment. My example is below<
nmap -sS -p 21,22,23,80,139,145,443,445,1433,3389,5900,8080 -T4 -A -v -Pn 192.168.70.234-235Nmap is open source, available from its website and in many Linux distribution software repositories.
HE tools on Android
On occasion, the only computing device I have with me is my mobile phone. Typically these times are when I need to check something out (a DNS record or firewall rule for example). HE Tools for Android are really handy because they allow me to conduct all sorts of tests from my phone:
- DNS lookups (essentially
nslookup) - TCP port scans (like
nmap) - Ping
- Trace route
- plus others
Additionally, my phone isn't on my office's corporate LAN so I can run a test from a different network without having to disconnect my laptop.
If you're a network engineer you'll find these tools really helpful, so I highly recommend adding them to your toolkit.
Banner image: Wireshark in use.

