Tales from the past: encryption and end users
A look at what can happen when organisations implement encryption.

Encryption is a powerful tool in keeping data safe - be that messages, bank transactions, shopping baskets, or even you just reading this blog. By encrypting data you reduce the chance of someone reading the data without permission. Law enforcements can have issues with encryption, as they equally cannot read the data of criminals, but we'll leave that debate for another time!
In this post I'm going to share two anecdotes of when organisations implemented encryption, but the way it was done led to some less-than-ideal user choices. These choices weren't the end users' fault, and were quite understandable albeit undesired.
"Encryption must be IT, right?"
The organisation had told people that encryption was being rolled out, and use of encryption and HTTPS ("look for the padlock") was becoming part of standard training. It's good that people have an idea that encryption exists, and what it means.
Unfortunately, technologies can be used for good and evil, and ransomware uses encryption to lock people out of their files. You may remember the WannaCry attacks from 2017, which caused problems for the UK's NHS (amongst others), and also more recent attacks in the news.
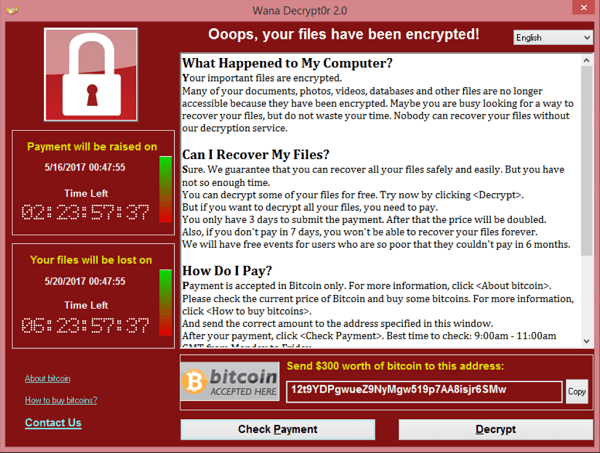
A colleague had unintentionally brought ransomware onto the network and it started to encrypt files. Knowing that IT used encryption, they just assumed this was legitimate IT department activity, because "I know you folk in ICT use encryption, so I assumed it was you and thus legitimate!". Not their fault, it was a reasonable assumption for a busy person to make after just glancing at the screen.
I wrote a bit more about this particular event in a blog post from 2020.
Complex decryption passwords
I've written before about how I prefer passwords to entered before decrypting drives (e.g. at boot), but it's important to consider the impact on the end-user. These passwords have to be entered every time, and for some people yet another password is not going to be well received.
IT generated unique secure (ish) passwords for each laptop, which became a standard part of their build process. We're talking things like xyC7548fin. As far as I know, there was no consultation with the users beyond communications that "you'll soon have to enter another password".
Sadly this led to a negative behavioural change. Previously, most staff didn't write their network credentials down - probably because they'd been able to choose (and change) their password. With these arbitrary passwords that were harder to remember, many staff took to writing the password on a postit note or sticker which they attached to the wrist rest. On explaining that their actions defeated the point of the encryption, they irritatedly explained the password was too hard to remember.
Communication is the key
As these stories show, communication is really important. Including ransomware, and what it looks like, in cyber security training might have helped prevent so much damage from the infection. Speaking to end-users before rolling out hard to remember passwords would have flagged that problem, and potentially prevented wrist rest password notes. These notes were a problem during an office break in - we had no idea if the stolen laptops had the password on them or not.
Let's all work together to be as safe and secure as possible 🙂.
Banner image: Something I and Microsoft Copilot threw together to act as a banner for my cyber security awareness month posts.

