Learning from cyber attacks
Cyber attacks are a regular occurrence, and it's important that we learn from them.
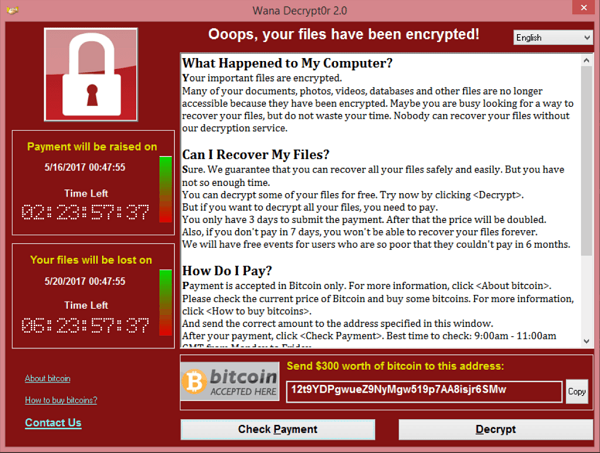
With cyber attacks a regular feature of an Internet connected life, it's fair to say they're almost now part of the Internet's "background radiation". Not all attacks are successful, but for those that are it's important that time is taken to learn from them.
For this post I'm going to focus on attack Copeland Borough Council, a local authority in the North West of England which I recently read a report about. While the attack itself took place in 2017, and was reported by BBC news, the report has only recently been shared (to me at least). I've not been able to find the report I was reading, as published by the Cabinet Office, but a similar report by David Cowan (ICT Manager) can be found here (archived here).
Please note, this post is not a criticism of Copeland. They have published their reports with the express intention that others learn from their experience.
What's ransomware?
Ransomware, including famous examples such as WannaCry and CryptoLocker, locks a user out of their files by encrypting them in place. As a result of the encryption the file is essentially random noise and won't open with the program that authored the file. After a while, the user is presented a ransom demand, requesting payment in order to unlock the files.
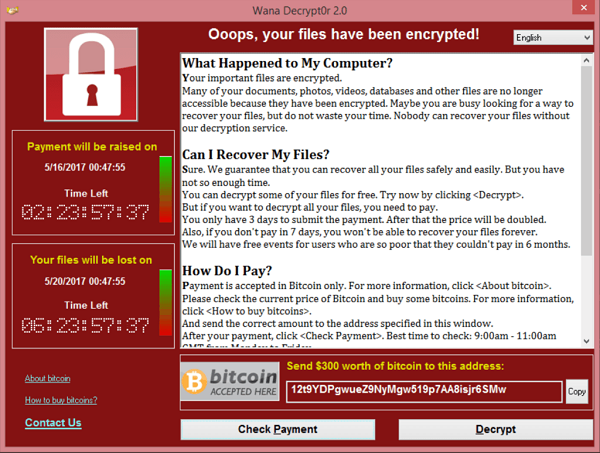
In the case of Copeland, the vast majority of their systems had been encrypted, along with some of their backups.
Impacts
The report highlights the impact of the attack in a number of areas, and I'll briefly cover some of these below.
Digital impacts
Of all the impacts, this is the most obvious. As a result of the attack the council were locked out of almost all of their ICT systems. Bear in mind that this means there's no access to ongoing case files, finance systems, the electoral role, and that use of any computers at this point would further the infection.
As there was due to be a by-election, lack of access to the electoral role was a huge problem.
Planning & house moves
Like many (most?) councils, searches for house moves and planning applications are handled via the ICT system. With the system unavailable, staff couldn't perform searches (in the UK, buying a house involves searches for sewers, geological features, Radon etc.) meaning house purchases and sales were held up. The report highlights this created a backlog which resulted in some people having to stay in hotels.
Payments
There was a risk staff members couldn't be paid, as the payroll and HR systems were unavailable. Understandably this meant staff were worried about bills bouncing, payments not going out, and the potential legal action that could follow.
Members of the public that are reliant on the payment of benefits were also impacted. This is an area the council focused on as it would have had a massive impact on the lives of those dependant on the payments.
Anxiety for staff
I'll be honest, I'd never considered the psychological impact a cyber attack would have on the staff team at large so I'm grateful to the report authors for making me think about this. Incident response teams will likely lose sleep over the attack, and work significantly longer shifts to get things resolved (I know I would) but it wasn't just those teams that suffered anxiety.
With most council operations having to revert to pen and paper, staff were left wondering how they could do their jobs - so much is computerised now. A colleague of mine, in a past job, has experienced this first hand when his workplace simulated an ICT failure. Staff that had been with the organisation for a long time could remember the paper methods, newer staff could not.
There's also anxiety caused by a sense of loss - at this point staff had to assume all their work was gone. I've not experienced a total loss of my files (hooray for backups) but I can tell you if I'd lost all my MSc while working on that I'd have been grieving, panicking and severely unhappy.
Lessons learned
Copeland invoked their emergency procedures but these hadn't been designed to include the total loss of the ICT system. They've since taken steps to improve their plans based on what they discovered. It's worth noting the old adage of "no plan survives contact with the enemy" [2] is true in cyber security too, as, apart from anything else, you cannot plan for every eventuality. Plans should be regularly reviewed and updated.
The public were informed of the problem early on, three days into the incident. While there was no doubt a temptation to hide the problem it was ultimately the right move to make people aware: Copeland benefitted as the public were understanding and patient.
Communication remained important throughout the problem and staff commented that sometimes information "from the top" was confused or slow to arrive. We need to remember that the organisation has a large number of staff, so getting information to everyone will have been slow. This likely sped up as the incident progressed but any plans should include communication strategies.
People are an organisation's greatest asset so their well being should be one of the top priorities, if not the top one. Emotional support was provided to staff, and I believe is ongoing. This is really good to see.
Conclusions
Copeland's systems were out of action for ten weeks, with other systems unavailable for longer. They were running up-to-date anti-virus software but they were still not safe. (Traditional) Anti-virus software will only protect you after the first strain of malware has been detected by the vendor and a definition file created, the same as the human immune system works.
The human impact is far wider reaching than I was expecting and shows how much we rely on computers. That's not a criticism, but it does mean we should fold steps to support everyone during the incident, not just those at the cyber response coal face, into our overall plan. Interestingly the report indicated it was the personal networks of the staff that helped in a number of cases, as staff relocated themselves to nearby council offices where they had contacts. Maintaining good relationships with partner organisations is essential (both personally and corporately).
Where possible, segment your networks to prevent the spread of malware. Additionally, test your business continuity plans and update them based on your findings. Keep your backups separated from your live / production data so they are not also negatively impacted by the attack.
Sadly, when it comes to cyber attacks, it's more likely to be a case of when you're successfully attacked, not if.
Banner image: WannaCry screenshot (see [1])
[1] WannaCry screenshot from Wikipedia, originally from https://securelist.com/wannacry-ransomware-used-in-widespread-attacks-all-over-the-world/78351/
[2] Helmuth von Moltke the Elder is attributed with this quote

