A QBot near miss, and a look at what might have been
A look at some malware that would have been delivered to a colleague, but they noticed something dodgy was happening!
"Good afternoon, might have a bit of a crisis. I think Bethany might have downloaded something suspicious/malicious."
I made a mistake this week - I checked my work phone for messages while I was on lunch. The above message greeted me: details of a possible malware infection and thus stopping lunch immediately I'd finished reading that message.
To be clear, I'd always rather be interrupted (or woken up) if there's malicious activity going on in our systems. I'm not "on call", but if I've got the choice between knowing now or knowing several hours later, when the damage is done, I'll accept the interruption and start incident response.
In this blog post I'm going to cover what happened during the incident, which fortunately was a near miss. My colleague didn't download a malicious payload but at the time of the message that was not clear. I want to start by praising "Bethany" for taking the correct course of action - she reached out to her manager to check what was happening and get help.
So, let's look at what happened.
Initial contact
It comes as no surprise that the attacker's initial contact was via email. Businesses get a lot of email so that's not a huge red flag. This particular email also seemed to carry on a conversation that was being forwarded to Bethany. Reading the email the recipient is invited to click a link to download more information. I'd imagine the website was an innocent bystander that got compromised - I've redacted the address, but you get the idea: hxxps://REDACTEDsolutions[.]com/usni/index.php?neequ=5.
Clicking the link downloaded a PDF, which at the time of clicking was not detected as being malicious. Indeed, passing the PDF through Virus Total showed it was safe in itself, but that's because it's just an invitation to download "encrypted attachments" - those aren't altogether unusual either [1]. Looking at the PDF it does look dodgy - wrong colour scheme for a start, but other than being a malicious invitation the PDF file is actually safe. Personally, I'd be quite annoyed if a product felt the need to tell me I'd got a "secret password", as that's the point, but psychologically I suspect people like knowing a secret so maybe the attacker is hoping to play on that.
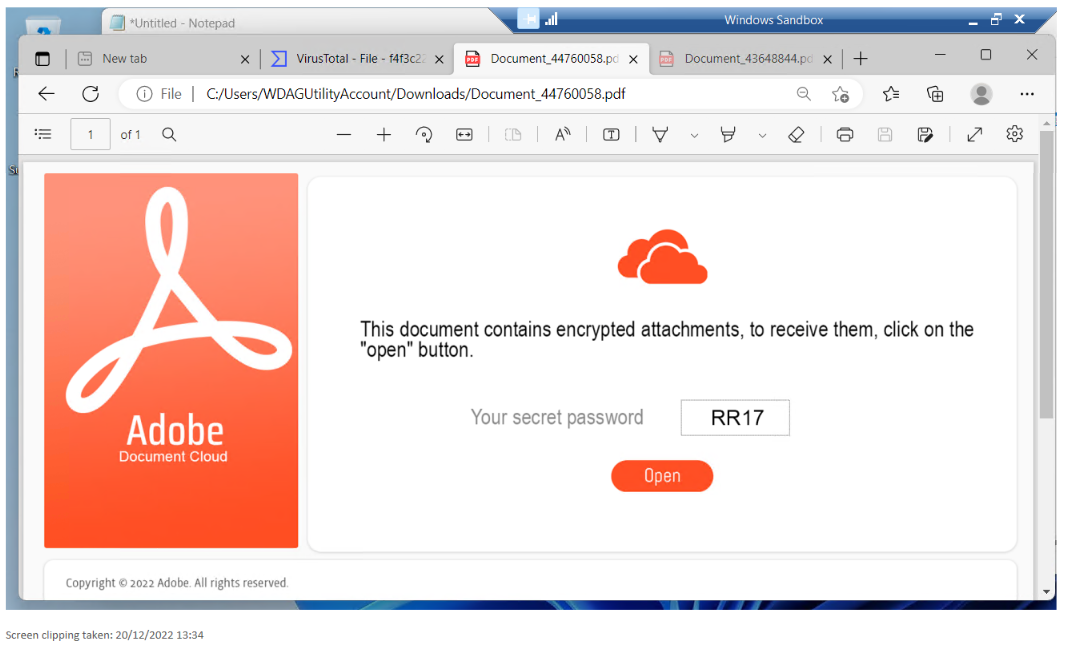
Bethany stopped at this stage, noticing that this looked dodgy, and called for help. I thanked her for that.
The "encrypted attachments"
After clicking the "open" button to receive our "encrypted attachments" a zip file downloads from a suspicious looking location. The address was an IP address hxxp://45.XX.146[.]200/C.zip which is never a good start. Note that the file to be downloaded is C.zip, but you're actually given a file called Summary_1764285_12202022.zip.
Opening the zip file we can see there's one file inside, Summary_1764285_12202022.img, which looks like it's a disk image file.
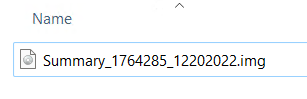
Extracting the zip file requires a password (RR17 from the initial PDF) which we can then double click to open. This "mounts" the file to make it accessible to Windows, and we can view the contents in Windows Explorer under "computer". Initially I could only see one file, a shortcut called Summary_1764285_12202022.lnk. In the screenshot that's the yellow star shaped icon. I chose to "show hidden files" and we can immediately see a second file, Nlsdl.dat.
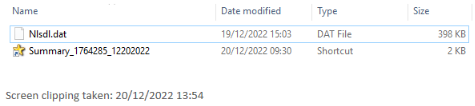
Looking at the file modification dates, if they're to be believed, this malware was put together on the 19th and 20th December at 15:03 and 09:30 respectively.
Note this is a big red flag - it's not normal for (most) businesses to receive disk image files that contain shortcuts for the user to click.
What does the shortcut do?
Viewing the properties of the shortcut I can see that it calls %SystemRoot%\system32\rundll32.exe \Nlsdl.dat,DrawThemeIcon. rundll32.exe is a standard Microsoft Windows component, and on its own is not malicious. Its purpose is to execute other libraries, often DLLs (Dynamic Link Libraries) but you can pass other files to it. The shortcut says "run rundll32.exe and load Nlsdl.dat into it". A quick look in a hex editor allowed me to confirm that Nlsdl.dat contained a Windows binary - it started with MZ.
Is the disk image detected as malicious?
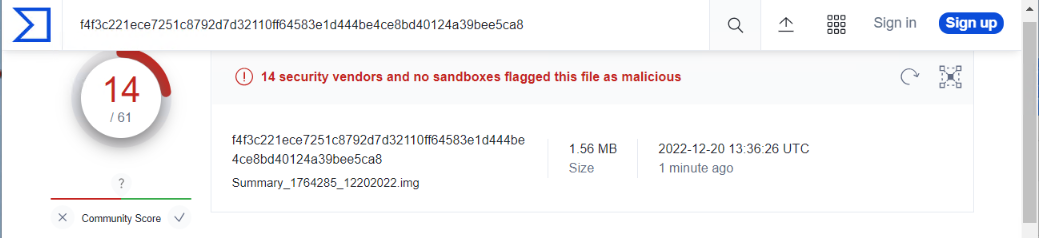
Returning to Virus Total I uploaded the .img file and it was detected as malicious. At the time of submission, only 14 of 61 detection engines flagged the file as malicious, and there's a number of different names for the malware. Some look like placeholder names but the one that stood out for me was Backdoor: QBot.
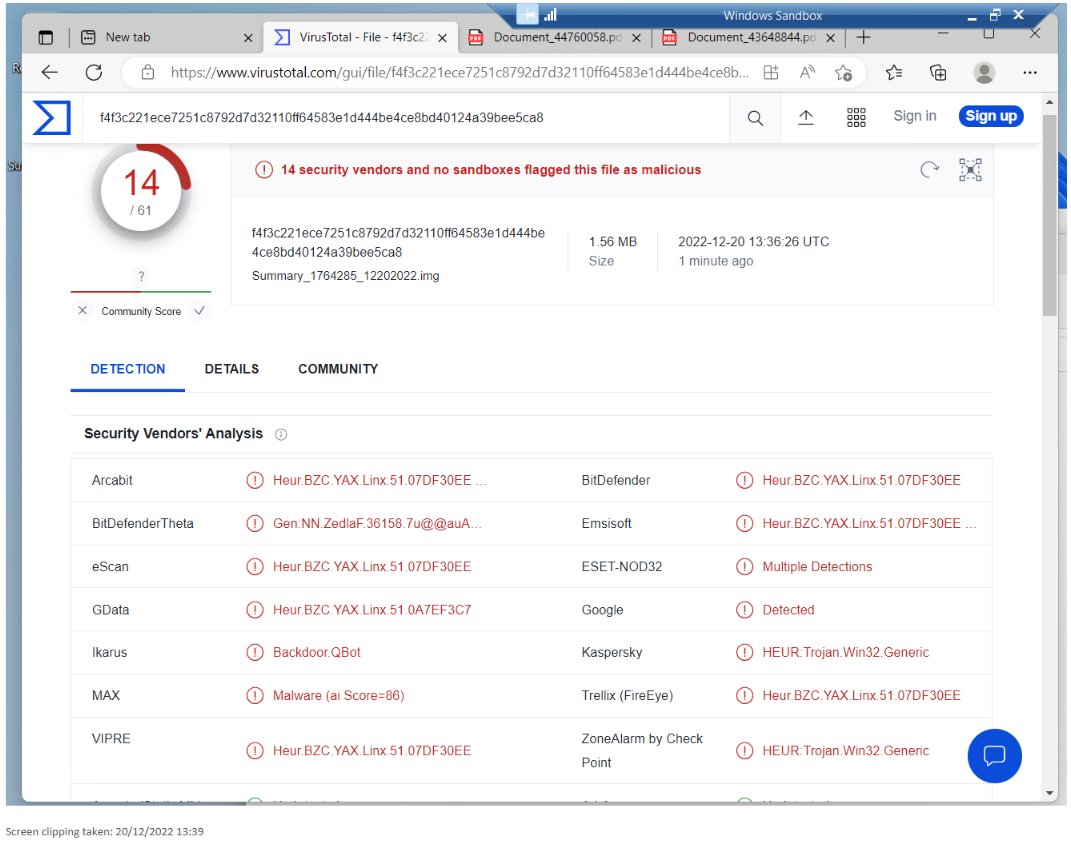
QBot has been around for years. Malwarebytes says Qbot is part of a family of trojans that have been around since 2009. The US Healthsector Cybersecurity Coordination Centre (HC3) also released a report on Qbot in 2020. Qbot can do a lot of things, including dropping ransomware programs.
Looks like we had a lucky escape 😊.
What if you run it?
Well there's no point having the lab otherwise! Double clicking the shortcut caused a tiny window to appear in the top left of the screen. Nothing else came up. Using procmon to see what had happened I could see some files had been created, but nothing else continued to run. It may be that the malware detected it was in a lab environment, so aborted. Alternatively it needed an Internet connection to continue and the lab virtual machine was cut off from the network so that failed.
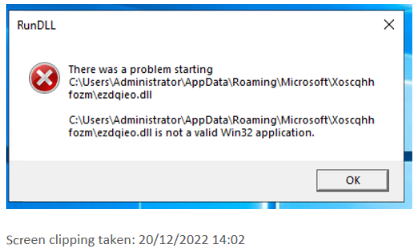
Rebooting the machine gave me a error after logging in. The path mentioned in the error message didn't exist on the system prior to the investigation (not did the error message), so this definitely was part of the infection.
The "kill chain" summary
- Contact end user by email
- Invite user to click a link
- PDF downloaded
- User reads PDF and clicks the link to download more details
- Password protected zip file is downloaded
- User extracts the zip, using password from the PDF
- User double clicks the extracted disk image file, mounting it
- User double clicks the shortcut in the mounted disk image
rundll32.exeloads in the malicious payload and performs action on the victim's computer
Tools
As part of the investigation I was using an isolated machine running some further isolated virtual machines. This isn't my full lab environment, but the tools were:
- Windows Sandbox
- Hyper-V
- Virtual machine of Windows Server 2019
- Frhed (a free hex editor)
- Microsoft Sysinternals Procmon
Conclusions
User training works. That's a big take away for me. My colleague encountered a problem, stopped, and phoned for backup. The alternative was continuing anyway and infecting us and I'm pleased to say that didn't happen.
Next - make sure you, as a security team, are approachable. Security professionals have a bad reputation for providing "no as a service" or being grumpy / unhelpful. Don't get me wrong, I can certainly be grumpy, but I do try to make sure I'm approachable. Making sure people feel comfortable reaching out to you is really important for reducing the impact to your organisation.
Oh, and if investigating live malware make sure your lab is isolated from the organisation's network and that you can return it to a known clean state afterwards!
Banner image: Screenshot of the Virus Total finding of a malicious file.
[1] I'd much rather receive a PDF document telling me to download my encrypted attachment than an HTML file (I'm looking at you Office 365 email encryption). Obviously I'd rather just have a plain text email with the link though...
Disclaimer: This post was written in my own time. While the screenshots above are from the investigation there is no proprietary or sensitive information in them.
Names have been changed to protect the innocent. I quite often pick Bethany Drake (and friends) as she was the lead character in the Antares trilogy of novels by Michael McCollum.

