Playing with some old malware
Malware has been around for ages, but how do some old malware samples work on more modern Operating Systems?

It's no surprise that malicious software, malware, is not new. I'll leave the reader to look up the history of malware, and there's plenty of material on the subject. Malware is also not going away, and I recently blogged about a near-miss with a strain of Qbot.
For this blog post I'm going to look at some old malware samples on different Windows operating systems. I've got three samples to work with and this post will focus on hotfix.exe. Check back for a future post to see sample #2.
The lab
For this my lab consists of four virtual machines:
- Windows 10 (1703)
- Windows Server 2008r2
- Windows XP Pro
- Windows 98 Second Edition
In all cases I've disabled automatic updates and the malware is being run on them straight after installation. Given that I'm playing with malware, and I'd rather not infect the rest of my devices, these virtual machines have no network or Internet access.
Each virtual machine has a snapshot taken just after the initial operating system (OS) build so I can revert to a clean state as and when required.
Built in anti-virus
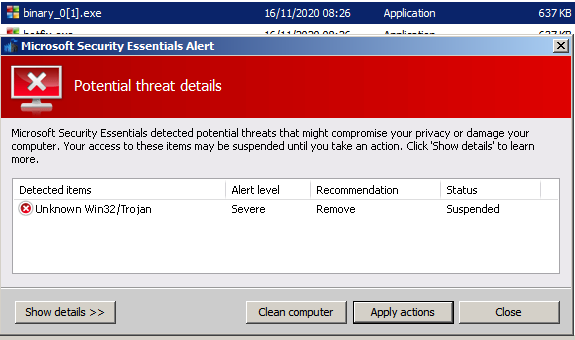
For Windows Server 2008r2 and Windows 10 there is Microsoft Security Essentials / Windows Defender (what Microsoft Security Essentials became) built in, so I've had to disable the antivirus. A screenshot of Windows Defender blocking access to my disk image containing the malware samples is below.
Test process and tools
I've copied some tools to C:\tools and I am running the malware from the desktop. This is to make sure the malware has a writable location once it starts running, as I'm delivering the malware to the VM via a CD disk image. There's also a small selection of files in the Documents / My Documents folder to see if the malware changes them in any way (it didn't). My chosen tools are:
- Oracle Virtualbox - runs the VMs
- Sysinternals Autoruns - to see if the malware adds any autorun instructions
- Sysinternals Process Monitor - also known as
procmon, shows every system call made so we can track what the malware does - Sysinternals Process Explorer - also known as
procexp, and just a fancier version of task manager
The samples
My three samples come from around 2010 following some clean up operations I'd performed at the time. Looking at the files, one sample came from a friend and another seems to have come from when I worked at a secondary school (a few students came to me with infected memory sticks back then).
Looking at the SHA1 hashes of the files, binary_0[1].exe and hotfix.exe are the same file, just with different names, so that brings me to two samples total.
jonathan@linux:~$ sha1sum ~/danger/*.exe
a49059653c2732a73d4394e2c548a17316f67a6e binary_0[1].exe
a49059653c2732a73d4394e2c548a17316f67a6e hotfix.exe
b9d625dd4b820ef4f71466107405e3d3129dcec2 pdfupd.exeRunning the samples through Virus Total gives us the names of the malware I'll be playing with. I'm using the names according to Sophos:
binary_0[1].exe/hotfix.exe- Troj/FakeAV-BTUpdfupd.exe- Mal/Emogen-Y
Running hotfix.exe
Let's start by looking at hotfix.exe, or Troj/FakeAV-BTU. The name tells me this will present me with some form of fake antivirus that will entice me to do something.
Windows 98 Second Edition
Sadly we're not able to evaluate hotfix.exe on Windows 98 SE as the "file expects a newer version of Windows":
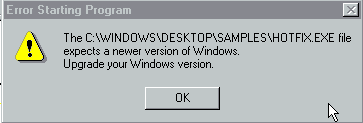
The lastest Sysinternals tools don't run on Windows 98 either.
Windows XP Professional
From memory, this was the OS that I took these samples from so I'm hoping we see something more exciting here. Sadly I couldn't run any of the Sysinternals tools on XP either - "not a valid Win32 application". On the plus side (for this research) I got immediately warned my computer may be at risk due to missing antivirus:
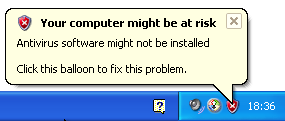
I infected the machine by running hotfix.exe and Windows Explorer was opened automatically, showing me "My Computer". Nothing else obvious appeared to happen.
I didn't realise that my installation of XP SP2 had Security Essentials built in, and after a brief period I got an alert that running the malware was blocked. This is amusing given I'd earlier been given a warning that antivirus software was not installed.
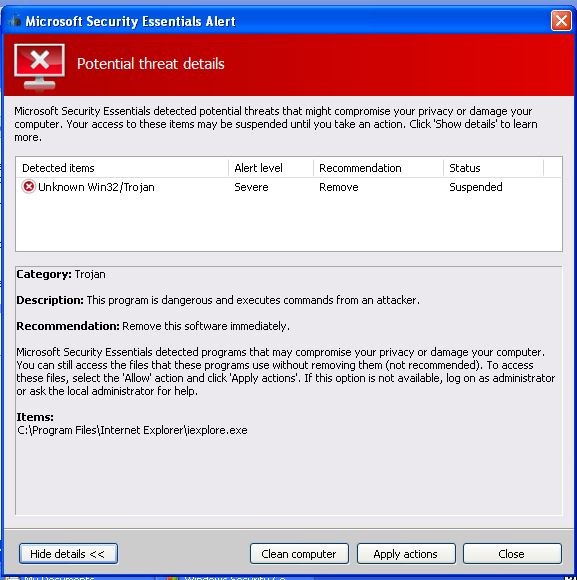
What was interesting that the alert appeared after attempting to launch various programs:
- Task manager
- Outlook Express
- Registry editor
Each time I ran an application, Security Essentials told me the infected program was whatever I'd tried to run. This was starting to feel familiar.
Solitaire still ran though, so at least I could play a game while my machine was infected. I've seen this behaviour before when malware has infected a machine and tells Windows that every time an executable is run it needs to be run via the malware - a way for the attacker to cripple the machine except for the tools needed to get help from the attacker.
I restored to my clean state and created a second user on the computer. I then infected my first user and experienced the same behaviour - nothing showing on screen but only few programs would run.
Next I switched to my secondary account (aptly named rescue). This user could still run programs such as task manager and I was able to mount the registry hive (settings) for my main account (C:\Documents and Settings\Jonathan\ntuser.dat). From there I browsed to KEY_USERS\jonathan\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\Shell and indeed Windows was being told to run everything via hotfix.exe, stored at C:\Documents and Settings\Jonathan\Application Data\hotfix.exe.
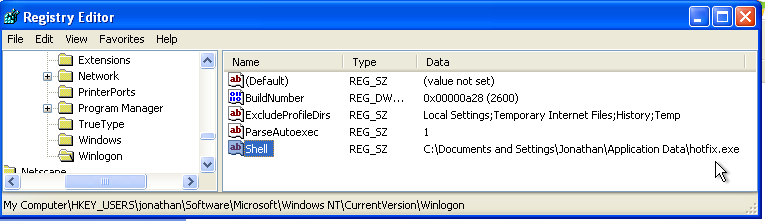
Security Essentials kindly cleaned up the threat and returned my original user to a working state, albeit leaving the nasty registry key intact.
Using old versions of Sysinternals
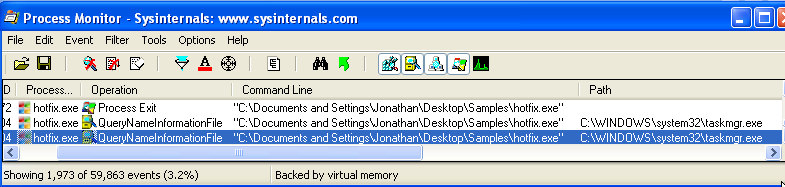
Fortunately the Wayback machine allowed me to obtain an old version of the Sysinternals suite. After infecting the machine and attempting to run procexp Windows crashed almost imediately, giving a dark blue screen of death before rebooting. Trying again, this time with procmon and we can see that when I attempted to start task manager the command line was actually using the hotfix.exe in my user profile:
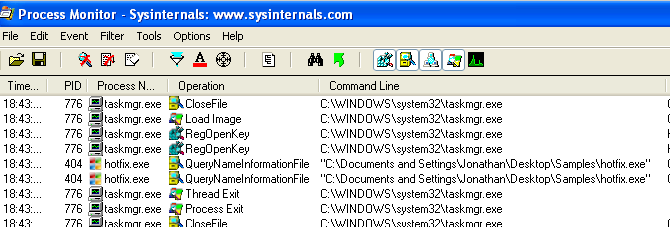
Reducing the filters we can actually see that task manager (taskmgr.exe) started but that as soon as hotfixe.exe kicked in task manager closed again:
Windows Server 2008r2
I wasn't able to run the latest procmon or procexp on this Windows Server 2008r2 build - either OS components were missing or the file was signed using a certificate the OS didn't trust. However, I was armed with my trusty old version of procmon via the Wayback machine.
After running hotfix.exe a file explorer window opened, much like it does on Windows XP. There's no other activity showing on the machine, but the hotfix.exe process continues to run. Loading up autoruns shows us the same change as Windows 10 (screenshots below). Unlike Windows XP though, I was still able to run task manager and other programs, despite the registry key being set - procmon had captured the action of setting it:
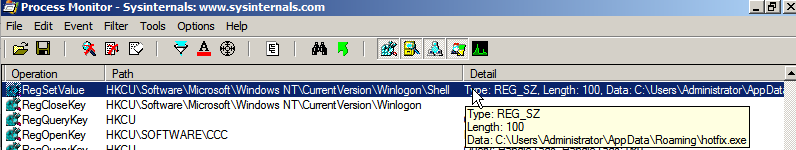
I could probably run programs because the file didn't exist at C:\Users\Administrator\AppData\Roaming\hotfix.exe for some reason.
Overall, nothing exciting to see in this VM.
Windows 10 (1703)
Running hotfix.exe opened a file explorer window and then seemed to stop running (based on procmon). In procmon I can see the file ran for about one minute before a thread exit event was logged, but according to procexp the file was still running in the background. About a minute later there was another thread exit event, yet again the file continues to run.
Nothing seemed to happen after that so I checked autoruns and there is a key that's been created that attempts to set my user shell (the registry value at HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\Shell):
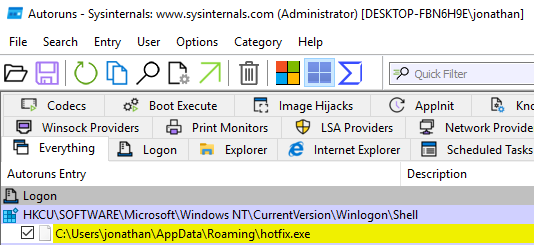
The line is yellow, which means "file not found", and we can validate that by looking at the path C:\Users\jonathan\AppData\Roaming\hotfix.exe - the file is indeed missing. In my clean environment the ...Winlogon\Shell registry value doesn't exist.
It looks like this malware doesn't run very well on Windows 10. There's even evidence in the registry that the Windows compatibility assistant attempts to help the malware to run correctly.
So long hotfix.exe
While it was fun seeing how this malware behaved, it was sadly not as exciting as I'd hoped for (that probably says a lot about me!). Almost entirely "nothing to see here", whereas I'd been expecting to see a fake antivirus screen warning the user of infections and demanding payment in order to fix the issue. Maybe I'll do some further analysis to discover if there's more to see.
Banner image: Screenshot of the malware sample icons.

