BIOS passwords - do we still need them?
BIOS passwords - to set or not to set, that is the question.
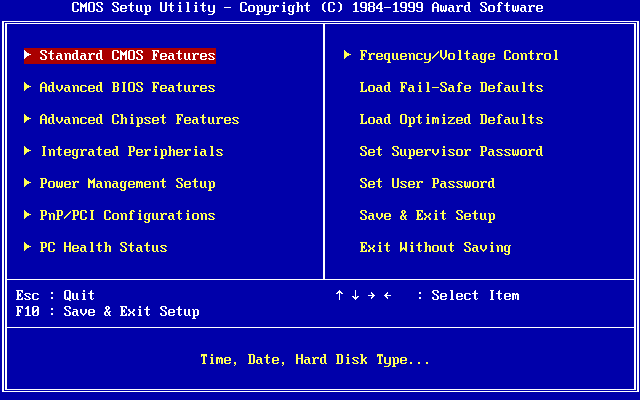
For years my standard approach has been to set a BIOS (or now UEFI) password on my devices, but time moves on and security practices should evolve. This post is a collection of my thoughts for and against setting BIOS passwords - the reader should make their own decision. Note this post is not about passwords / PINs used to decrypt storage devices.
For ease, I will refer to BIOS, but the same thoughts apply to UEFI.
What is BIOS or UEFI?
Before your computer loads your operating system (OS), like Linux, MacOS, or Windows, the BIOS provides a very Basic Input / Output System to allow the computer to start. The BIOS tells the computer where to look for an OS and controls certain hardware settings such as whether the built-in devices should be enabled. You could, for example, disable the built-in sound and network cards. Boot order, the devices the computer will look to load an OS from, are also specified in the BIOS.
As part of the boot process, the BIOS will often perform a Power On Self Test (POST) to check the RAM (memory) and configure the hardware appropriately. Generally these tests are hidden behind full screen logos these days, but they didn't used to be! Watching your computer check every kilobyte or RAM you had could take a while...
Your computer's BIOS or UEFI is stored in a chip on the computer's motherboard, and is sometimes called firmware. Often we talk about printers and other "non-computer" devices having firmware rather than BIOS, but arguably they still have a BIOS (and they are still computers!).
There's more detail on BIOS on Wikipedia.
What is a BIOS password?
Much like when you login to your computer's OS, you can set a BIOS password. Often there are two levels of privilege within the BIOS - user and administrator. Passwords can be set for either level, and what's allowed without the password varies between BIOS manufacturers. Setting a user password might stop someone seeing the configuration at all, or may allow some settings to be viewed and minor changes to be made. BIOS administrator passwords protect the more sensitive, or damaging, settings from modification.
Depending on the BIOS manufacturer, how you enter the password will vary. Some newer BIOSes have a lock icon that has to be clicked [1] to provide a password prompt. Others present a password prompt on entering the BIOS and the password you use determines the privilege level (user or administrator).
Why set a BIOS password?
Stops tampering
When I worked in a school this was the biggest reason for setting a password - pupils liked to tamper with settings. By setting a password I could ensure the computer would boot in a consistent way each time, stopping a pupil from setting the boot order to "floppy disk" for all three boot priorities. Doing that didn't damage the computer or the OS, but it did mean that the computer wouldn't boot to Windows automatically, instead leaving the next user with a "Boot device not found" message.
Boot order wasn't the only setting I wanted to protect of course. Earlier I mentioned disabling built-in hardware - imagine having a whole classroom with built-in network cards suddenly disabled. Not a helpful scenario 🤣.
Prevents alternative OS booting
By changing the boot order in the BIOS it's possible to plug in a USB memory stick or provide a CD / DVD (remember those?!) to boot the computer from. In a regulated environment, or one where you need to apply controls for safeguarding reasons (like a school), you need to ensure all the computers are running the OS that you've configured and locked down appropriately.
Adding a BIOS password allows you to prevent changes to the boot order, and removes access to the boot menu that could be used to boot from an alternative device once.
It used to be that booting from an alternative OS, particularly Linux, would allow you to change files on the installed OS. I've booted Linux from a CD a number of times to make repairs to a Windows installation. Equally, you could boot from an alternative OS in order to collect files from the installed OS on the machine, without needing to know a password, leaving little evidence that you'd done so. Obviously there is nothing to stop someone taking the hard disk / SSD out of the computer and using a device they controlled to get the files though.
What's changed then?
Encrypted disks
This is probably the biggest change that's made me alter my thinking on BIOS passwords. With the increasing availability of encrypting disks (BitLocker on Windows, FileVault on MacOS, LUKS on Linux) there's less risk someone will boot an alternative OS on the computer to then steal files.
Given the OS and storage in the computer is protected by encryption, I'm less concerned someone will make a change in the BIOS in order to access files.
Working from home / support
Some of you were working in IT on the 19th July 2024 when "the CrowdStrike incident" caused 8.5 million Windows computers to fail to boot. Others will remember the world seeming to grind to a halt, with flights delayed, doctors' surgeries moving to pen and paper, and just a whole load of chaos. Computers needed manual intervention to fix the problem, and with many people now working remotely from their IT teams, there were a lot of phone calls that day!
For some of my colleagues, the fix involved taking them into the BIOS to change a setting [2] so the recovery environment could see the Windows drive and we could apply the fix. With a BIOS password set, colleagues were unable to make the change without me giving them the password.
"No problem", you may be thinking, "just change the password afterwards". I agree this is good practice, but the original problem of the colleague being remote remains. It may not be practical for the colleague to come into an office, meet with the IT team, and have the password changed.
With that in mind, the presence of the BIOS password, if unshared, would have meant the colleague still couldn't work. Now that the colleague has the BIOS password its usefulness is reduced (the user can make changes). Was there a benefit from the password being present?
I'd say there was an argument for not setting a password on remote worker devices. The worst that would happen, assuming the hard disk is encrypted, is that they make a change that breaks their computer (e.g. stops it booting). A small impact, especially given most people never go in the BIOS anyway.
BIOS updates become automated
Tools like Dell Command Update allow BIOS updates to be installed easily, but only if the BIOS isn't passworded. You can configure the tool with the password, so it can perform the update, but this step is easily missed (and if the password gets changed, it has to be changed in the tool too). Configuring the password in the system updater tools becomes harder again if the password for each BIOS is different (it should be), meaning it's not easy to push a single configuration to every device.
Conclusion
Ultimately it's entirely your decision as to whether you set a BIOS password or not. I'd suggest in environments where the user is likely to tamper and there are static computer rooms / labs (schools, universities) that it's probably worth a BIOS password.
Where the scenario is adult employees (or people you can reasonably trust, at least a bit...), that are likely remote for some or all of the time, so long as the storage is encrypted it's possibly not worth setting a BIOS password any more.
It's correct to say that setting a BIOS password will reduce the attack surface of the device. You need to decide if that reduction is a benefit to you and your organisation.
On my personal devices I'll probably still set a password, but then I provide my own IT support!
Banner image: By Award Software International Inc., recreated by User:Kephir - Self-made, by extracting the bitmap font from the video ROM and recreating the screen character by character. Based on an actual setup screen of a computer I (User:Kephir) once had. The color palette may be a bit inaccurate, but otherwise it is probably the closest thing to a screenshot one could ever get with this kind of software., Public Domain, https://commons.wikimedia.org/w/index.php?curid=20331445
[1] Newer BIOSes, and many UEFI environments, have full mouse support.
[2] The storage mode for their internal drive - RAID to AHCI.

